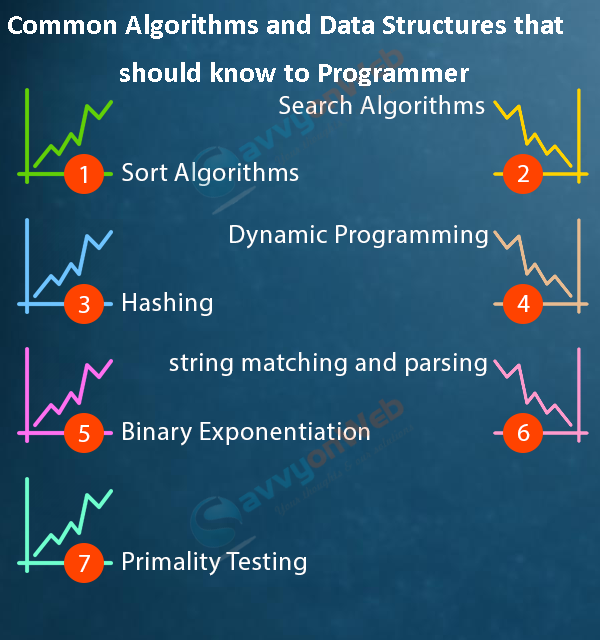
Common Algorithms and Data Structures that should know to Programmer
In software engineers life algorithms and data structures is most vital subject on the off chance that they need to go out in the programming scene and make a few bucks. Today, We will see what they do and where they are utilized with least complex illustrations. This rundown is arranged remembering their utilization in focused programming and current advancement hones.
1. Sort Algorithms
Sorting is the most intensely contemplated idea in Computer Science. Thought is to organize the things of a rundown in a particular request. In spite of the fact that each real programming dialect has worked in sorting libraries, it proves to be useful on the off chance that you know how they function. Contingent on prerequisite you might need to utilize any of these.
Merge Sort
Quick Sort
Bucket Sort
Heap Sort
Counting Sort
All the more essentially one ought to know when and where to utilize them. A few illustrations where you can discover coordinate utilization of sorting procedures include.
Sorting by value, prevalence and so forth in e-business sites
2. Search Algorithms
Binary Search (in linear data structures)
Binary Search is utilized to perform an extremely effective pursuit on sorted dataset. The time intricacy is O (log2N). Thought is to more than once partition fifty-fifty the parcel of the rundown that could contain the thing, until we limit it down to one conceivable thing. A few applications are-
When you look for a name of melody in a sorted rundown of tunes, it performs binary inquiry and string-coordinating to rapidly give back the outcomes.
Used to investigate in git through git bisect
Depth/Breadth First Search (in Graph data structures)
DFS and BFS are tree/diagram navigating and seeking data structures. We wouldn't dive deep into how DFS/BFS work however will perceive how they are diverse through after activity.
Applications
Utilized via web crawlers for web-creeping
Utilized as a part of computerized reasoning to manufacture bots, for occasion a chess bot
Finding most brief way between two urban areas in a guide and numerous other such applications
3. Hashing
Hash lookup is presently the most generally utilized procedure to discover fitting data by key or ID. We get to data by its file. Already we depended on Sorting and Binary Search to search for record though now we utilize hashing.
The data structure is alluded as Hash-Map or Hash-Table or Dictionary that maps keys to values, productively. We can perform esteem lookups utilizing keys. Thought is to utilize a suitable hash work which does the key - > esteem mapping. Picking a decent hash work relies on the situation.
Applications
In switches, to store IP address - > Path match for steering instruments
To perform the check if an esteem as of now exists in a rundown. Direct pursuit would be costly. We can likewise utilize Set data structure for this operation.
4. Dynamic Programming
Dynamic programming (DP) is a strategy for taking care of an unpredictable issue by separating it into more straightforward subproblems. We illuminate the subproblems, recollect their outcomes and utilizing them we advance toward take care of the unpredictable issue, rapidly.
Applications
There are numerous DP algorithms and applications yet I'd name one and clear you out, Duckworth-Lewis strategy in cricket.
5. Exponentiation by squaring
Let's assume you need to compute 232. Typically we'd repeat 32 times and discover the outcome. Consider the possibility that I let you know it should be possible in 5 cycles.
Exponentiation by squaring or binary exponentiation is a general strategy for quick calculation of extensive positive whole number powers of a number in O (log2N). Not just this, the technique is likewise utilized for calculation of powers of polynomials and square networks.
Application
Computation of extensive powers of a number is generally required in RSA encryption. RSA likewise utilizes measured number juggling alongside double exponentiation.
6. String Matching and Parsing
Design coordinating/seeking is a standout amongst the most critical issue in Computer Science. There have been a great deal of research on the point however we'll enroll just two essential necessities for any software engineer.
KMP Algorithm (String Matching)
Knuth-Morris-Pratt algorithm is utilized as a part of situations where we need to coordinate a short example in a long string. For example, when we Ctrl+F a watchword in an archive, we perform design coordinating in the entire report.
Consistent Expression (String Parsing)
Numerous a times we need to accept a string by parsing over a predefined confinement. It is vigorously utilized as a part of web advancement for URL parsing and coordinating.
7. Primality Testing Algorithms
There are deterministic and probabilistic methods for figuring out if a given number is prime or not. We'll see both deterministic and probabilistic (nondeterministic) ways.
Strainer of Eratosthenes (deterministic)
In the event that we have certain farthest point on the scope of numbers, say decide all primes inside of range 100 to 1000 then Sieve is an approach to go. The length of range is a pivotal component, since we need to designate certain measure of memory as per range.
For any number n, incrementally testing upto sqrt (n) (deterministic)
In the event that you need to check for few numbers which are inadequately spread over a long range (say 1 to 1012), Sieve won't have the capacity to distribute enough memory. You can check for every number n by crossing just upto sqrt (n) and perform a distinguishableness keep an eye on n.
Fermat primality test and Miller–Rabin primality test (both are nondeterministic)
Both of these are compositeness tests. On the off chance that a number is turned out to be composite, then it beyond any doubt isn't a prime number. Mill operator Rabin is a more refined one than Fermat's. Infact, Miller-Rabin likewise has a deterministic variation, however then its a session of exchange between time multifaceted nature and exactness of the calculation.
Application
The absolute most critical utilization of prime numbers is in Cryptography. All the more accurately, they are utilized as a part of encryption and decoding in RSA calculation which was the primary usage of Public Key Cryptosystems.
Another utilize is in Hash works utilized as a part of Hash Tables
We'll talk about some propelled algorithms each focused software engineer ought to know in the following post. Then ace the above algorithms or partake in the remarks about what you think each novice middle of the road software engineer ought to know.